Emergency Management Plan
Support Appendix - Mitigation
Mitigation Appendix AAa: Behavioral Intervention Team (BIT) Protocol for Internal Communication
- Members of the BIT are to contact each other in an emergency using pre-established, redundant e-mail and phone chains. This process is normally coordinated by the BIT Chair, who is notified of emergencies by UPD (who has determined that BIT has jurisdiction by protocol).
- BIT is not responsible for responding to reports of behavioral threats, and in circumstances where there is an immediate threat to life or property, UPD should be contacted by dialing 785-628-5304 or 911. UPD will respond, operating within statutory authority as the situation or circumstances occur.
- Members are to be contacted in regular, non-emergency situations by the Chair, using the e-mail and phone chain.
- The Center of Public Safety Conference Room is the default meeting location for convening BIT emergency/regular sessions.
- The BIT meets in regular (non-emergency) sessions each Tuesday.
- The Assistant Vice President for Student Affairs for Student Life is the permanent Chair of the BIT.
- The Assistant Vice President for Student Affairs for Student Support Services will fill in as Chair in the absence of the regular Chair.
- The Director of Residential Life will fill in as Chair in the absence of the Assistant Vice President for Student Affairs for Student Support Services.
- The Director of UPD serves as the permanent on-call BIT contact.
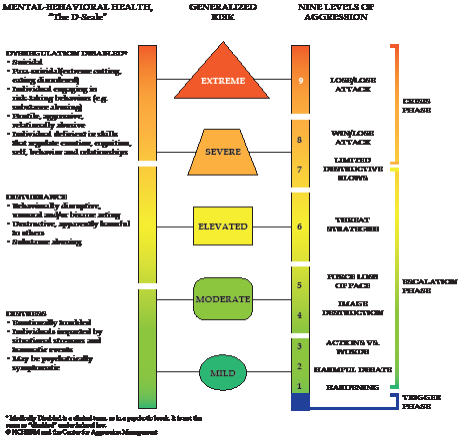
- Once a database system is complete, BIT submissions will be reviewed and assessed daily by members of the BIT committee, all of whom will have access to the database. Current practice is submissions are reviewed as submitted and discussed at BIT. Use the rubric to classify all incidents, and overlay Byrnes' 9-level scale, when a threat is suspected or detected)
- BIT is solely responsible for assessment of threats of incidents regarding students for which UPD does not have jurisdiction
-
- Determine how credible the threat is;
- Determine how serious the threat is;
- Does the person making the threat appear to have the resources, intent and motivation to carry out the threat?
- BIT uses the Aggression Management Risk Assessment continuum:
-
- Primal or cognitive aggressor?
- Assignment of level on Byrnes' 9-level scale
-
- Actions according to appropriate intervention described
- Written findings of objective, specific, plausible details:
-
- What was said? To whom?
- What was written? To whom?
- Do we know whether the person who heard/saw the threat is the object of the threat or a third party? Were they intended to see/overhear?
- What was done? How was it perceived?
- Where and when did it occur? In what context?
- Did witnesses observe this behavior?
- Why did the person act/behave in this way?
- Are the reasons for making the threat clear? What are they?
- Are there any indications of means, weapon or method? Target?
- Date, time or place?
- Concrete information about plans and/or preparation?
- The more detail, the higher you should rank the threat.
- Assessment of legal "true threat" and free speech issues (for evaluation of student writings and statements):
-
- A true threat is one a reasonable person would interpret as a serious expression of intent to inflict bodily harm upon specific individuals.
- Assurance of due process, to the extent possible, according to FHSU policy.
- BIT members should debrief interventions as a team, and once support structures are in place and resources are deployed, the concerning behavior relational to that event will be considered resolved unless there are other instances of concerning behavior that are brought to the attention of BIT. In the event of follow-up, the following questions may be asked:
-
- Is the person continuing in a course of therapy?
- Are support systems and services ongoing?
- Are friends helping to monitor?
- Is a behavioral contract functioning?
- Are other inhibitors to harm or self-harm in place?
- If follow-up and check-in reveals someone who is untethered from the mechanisms of intervention, the gap may be an indicator of a greater need for observation, check-in or further intervention.
- In the event of a student death, the Crisis Protocols for Student Death should be followed.
-
- Ensure IMT integration.
- Be aware of handling delicate release of information if death by suicide.
Mitigation Appendix AAb: Behavioral Intervention Team (BIT) Protocol for Reporting Incidents to BIT
- A report of behavior posing a concern but not rising to the level of an immediate threat to life or property or criminal violation should be made to the BIT, Office of Student Affairs, Director of Residential Life or UPD.
- All incidents or red flags are to be reported to BIT by ALL employees except those covered by privilege at the time of receiving the report or becoming aware of the incident. Privileged reports may be shared anonymously or confidentially, unless the report indicates a threat for which privilege must be breached. (Anonymously refers to omitting from the report the name of the person who holds the privilege or the names of any other person about whom the reporter gains information via a privileged relationship.)
- Employees who fail to follow the mandated reporting policy will face appropriate consequences.
-
- Incident reports of red flags are to be uploaded to the database (or otherwise reported to BIT) by employees within 24 hours of first becoming aware of the incident (if not sooner).
- As much detail should be included as you have, filling out all database fields.
- The following types of behaviors or actions should be reported, though the list is not exhaustive. Reporters are expected to use their judgment as to what is reportable, erring on the side of reporting if in doubt. For example, if an incident may seem minor but other similar incidents occur in close proximity, they may indicate a pattern not visible to the witness of a single incident:
-
- Extreme rudeness or insubordination to FHSU officials, staff, faculty, administrators or students.
- Classroom or workplace disruption
- Violations of university policy
- All violations of the student code of conduct
- Drunkenness in the classroom or in the workplace
- Threatening words or actions
- Writings that convey clear intentions to harm oneself or others
- Observed self-injurious behavior, such as cutting, burning, etc.
- Online posts on Facebook, MySpace, RateMyProfessor that are threatening
- Excessive class or work absenteeism
- Suicidality, including threats (I am going to kill myself), gestures (erasing one's hard drive), ideation (I've always thought about killing myself by jumping off a cliff), or attempts.
- Acts motivated by hatred, discrimination or paranoia that cause a person to mistakenly believe he/she is being targeted.
- Stalking
- Relationship violence (even if the victim doesn't want you to tell, unless the information is conveyed to you in a privileged relationship that does not pose an immediate threat for which privilege must be breached).
- Hazing
- Flat affect or extreme lack of responsiveness
- "Accidental" overdose
- Disappearances, kidnappings or missing persons
- Harassment
- Alarming references to bombs, ammunition or ordnance
- Alarming infatuation with fire or firearms
- Reporters should classify their report by the following risk or alert scale. Incidents receiving Severe or Extreme classification require not just uploading to the database, but a call to the on- call BIT member as well. Ultimately, BIT will classify the incident according to the National Behavioral Intervention Team Association Threat Assessment Tool.
- BIT must receive notification of all behavioral contracts formed between the university and the individual involved.
- Faculty must report all classroom (and other student) disruption incidents to the database, and potentially to the office of student conduct.
- Residential life personnel must report residence hall disruptive behaviors to the database, and potentially to the office of student conduct if they reach a threshold of severity that removes them from the residential life conduct process.
- Supervisors must report disruptive behavior to the database.
- Campus law enforcement may coordinate HPD and UPD log entry with BIT database entry requirements.